Welcome to the first in a series of articles specifically aimed at cybersecurity. The purpose of these articles will be to create awareness of all things related to keeping things safe online (well, at least as safe as we can).
We live in a world where your life is hosted on a computer somewhere. Our day-to-day lives are broadcast across Facebook, Twitter, Snapchat and the like. And while there is a lot of good out there is cyber space, there are those who would and will use it to do a lot of bad stuff.
In the coming series I will explore some of the aspects of cybersecurity, and offer some clarity around buzz words such as phishing, vishing, smishing, social engineering and cat-fishing.
In this post, I explore phishing and share tips on how to avoid getting hooked by this type of scam.
How not to become phish food
Phishing is an attempt to convince the average Joe to freely give out personal information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication.
For example, you might receive an email from your banking institute claiming that they’re doing random security checks on all of their clients and they require you to type in your personal details. The email may look like the real deal, but it’s not.
Here are ten tips that anyone can use to minimise the chances of falling victim to a phishing attack:
1: What’s in a name
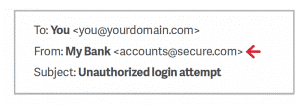
A common tactic that cybercriminals like to use is email spoofing, to spoof the display name of an email message.
Here’s how it works: If a fraudster wanted to spoof the hypothetical brand “My Bank,” the email may look something like:
Since My Bank doesn’t own the domain "secure.com," its domain-based message authentication, reporting & conformance (DMARC) protocol will not block this email on My Bank’s behalf, even if My Bank has set its DMARC policy for mybank.com to reject messages that fail to authenticate. This fraudulent email, once delivered, appears legitimate because most user inboxes only present the display name. Don’t trust the display name. Check the email address in the header from - if looks suspicious, don’t open the email.
2: No clickey
Hover your mouse over any links embedded in the body of the email. If the link address looks weird, don’t click on it. If you want to test the link, open a new window and type in website address directly rather than clicking on the link from unsolicited emails.
3: Check for spelling mistakes
Brands are pretty serious about email. Legitimate messages usually do not have major spelling mistakes or poor grammar. Read your emails carefully and report anything that seems suspicious.
4: Analyse the salutation
Is the email addressed to a vague "Valued Customer?" If so, watch out - legitimate businesses will often use a personal salutation with your first and last name.
5: Don’t give up personal information
Legitimate banks and most other companies will never ask for personal credentials via email. Don’t give them up.
6: Beware of urgent or threatening language in the subject line
Invoking a sense of urgency or fear is a common phishing tactic. Beware of subject lines that claim your "account has been suspended"” or your account had an "unauthorised login attempt".
7: Review the signature
Lack of details about the signer or how you can contact a company strongly suggests a phish. Legitimate businesses always provide contact details.
8: Don’t click on attachments
Including malicious attachments that contain viruses and malware is a common phishing tactic. Malware can damage files on your computer, steal your passwords or spy on you without your knowledge. Don’t open any email attachments you weren’t expecting.
9: Don’t trust the header from email address
Fraudsters not only spoof brands in the display name, but also spoof brands in the header from email address. More than 760,000 email threats contain spoofed brands somewhere in the header from the email address with more than two thirds spoofing the brand in the email domain alone.
10: Don’t believe everything you see
Phishers are extremely good at what they do. Just because an email has convincing brand logos, language, and a seemingly valid email address, does not mean that it’s legitimate. Be skeptical when it comes to your email messages - if it looks even remotely suspicious, don’t open it and delete it immediately
There are other types of phishing attacks to be aware of too, like whaling and spear phishing.
"Whaling" is a specific form of phishing that's targeted at high-profile business executives, managers, and the like - i.e. the big fish! It's different from ordinary phishing in that with whaling, the emails or webpages serving the scam take on a more official or serious look and are usually targeting someone in particular.
“Spear phishing” is a targeted phishing attack, such as targeting a group of users within a single organisation. While whaling is a form of spear phishing because it targets executives, all spear phishing does not target executives so whaling is a better answer.
There are a few other phishing exploits, like:
· “Vishing” - that’s phishing but carried out with phone calls
· “Smishing” - SMS phishing is one of the easiest types of phishing attacks
· "Search engine phishing" is the type of phishing that refers to the creation of a fake webpage for targeting specific keywords and waiting for the searcher to land on the fake webpage. Once a searcher clicks on the page link, they will never recognise that they're hooked - until it is too late.
While it can be scary to think who's lurking out there and how easily they can reel you in, if you follow these simple and common-sense steps, you can stay pretty safe online.
And remember, if you want to ensure you or our team have the latest security skills, we have a range of cybersecurity courses on offer.
About the author
Deon van Heerden an IT trainer at Auldhouse, based in Auckland. He has 20 years experience in the industry and is a cybersecurity specialist.
> Banner photo by Matt Hardy from Pexels